Cloud Defense
Industry: Cloud Security
Country: USA
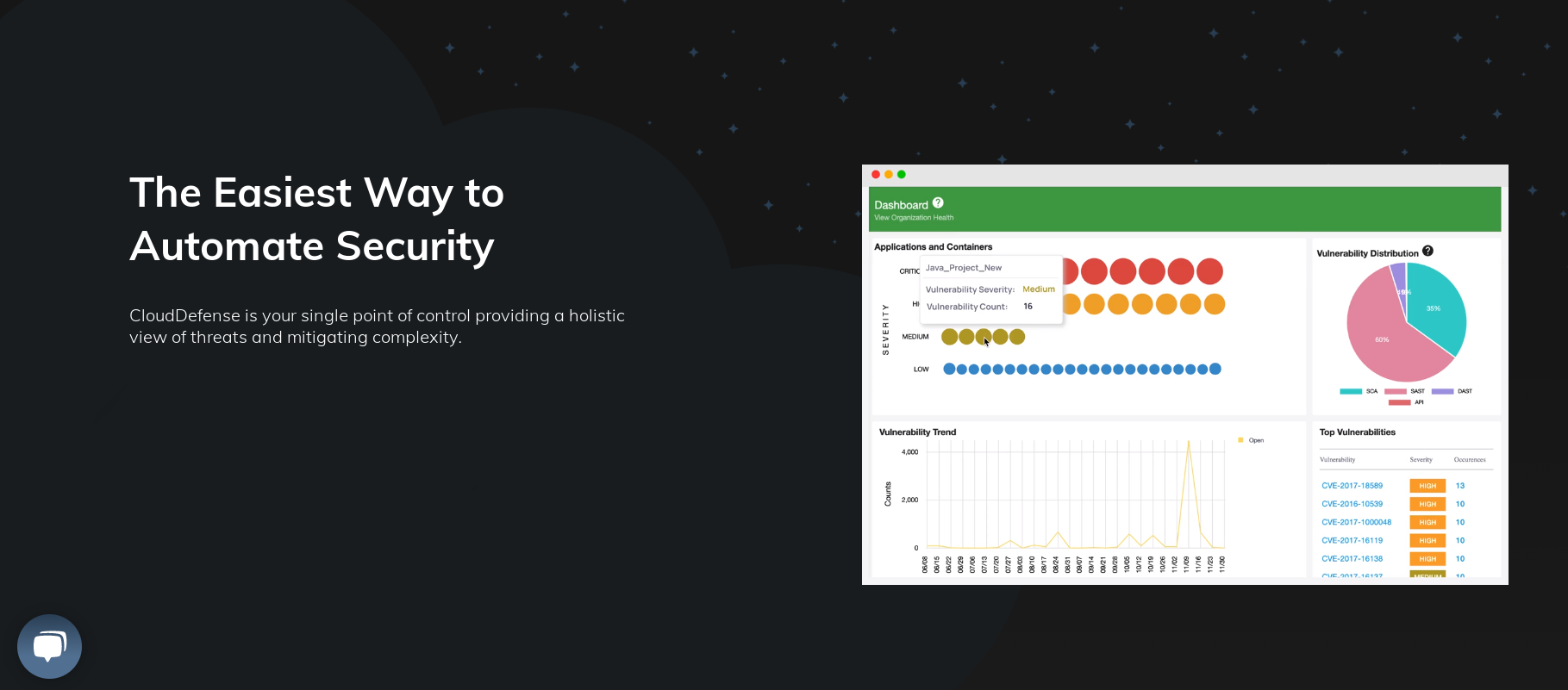
Description
The primary idea behind Cloud Defense is to check and find any vulnerabilities in client projects. This tool scans the code of projects, all dependencies that are used in the project (libraries), docker containers, and API for vulnerabilities. The benefit of this application is that it can be installed on your local computer or the cloud using the command-line interface (CLI).
So, whether your project is on your local machine or the cloud, you can still use Cloud Defense to scan for any vulnerabilities that it may contain. The commands used to install Cloud Defense vary based on the operating system you are running. Cloud Defense is supported by all the major operating systems, that is, Windows, macOS, and Linux.
Client goals
With this project, the client tasked us with supporting and improving the functionalities that already existed. We were also supposed to undertake the implementation of the new scanning functionalities and support for other services and customer bases. All these features were to be implemented while considering ease of use for all the application's target users.
Main roles
Super admin
The super admin has full access to the entire backend of the application and has the ability to create and view applications for all teams.
Team Admin
Unlike the super admin, the Team admin's level of access is a bit limited, and he only has the ability to manage and maintain a team.
User
The end-user has the least level of access, and all he can do is view their scanned team apps and download a detailed report to view the vulnerabilities in the scanned app.
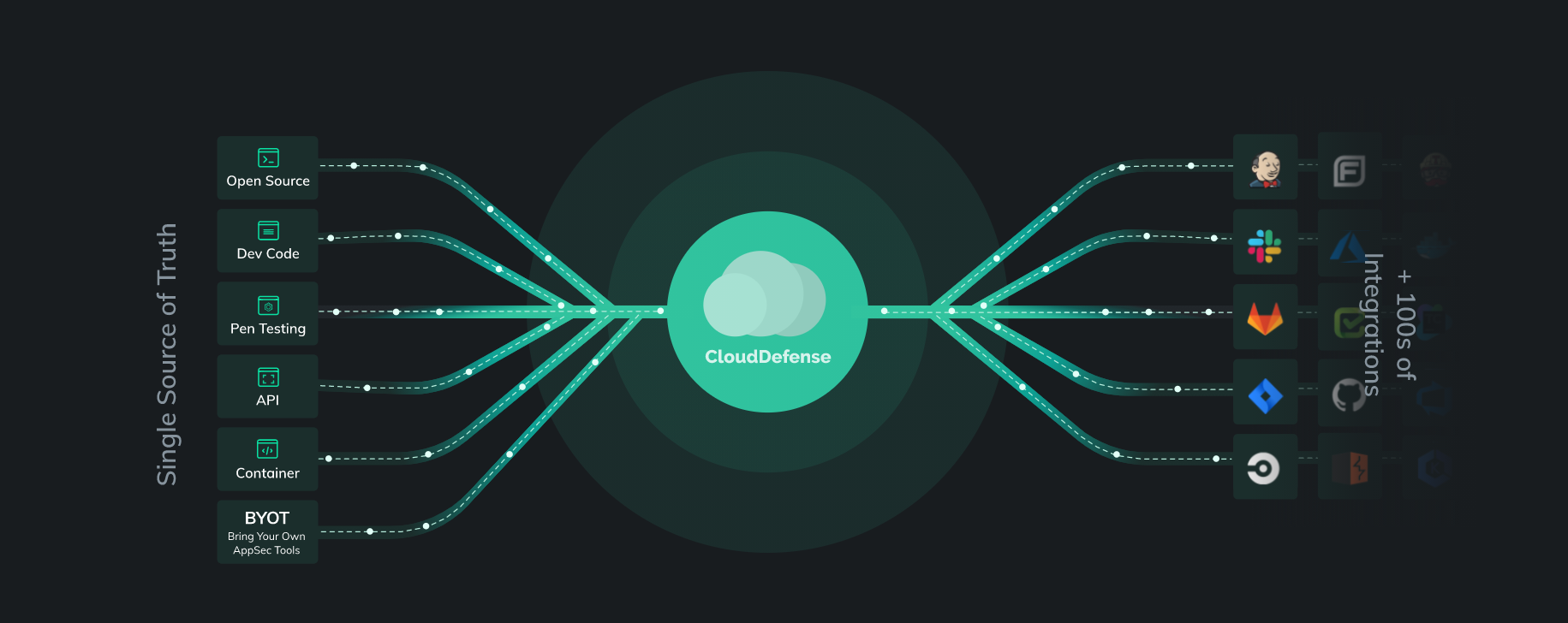
Implemented features
User management
On behalf of Inventorsoft, we took part in the process of authorization, registration, password resets, and updates. We participated in integrating the Keycloak chain into the application to ensure secure and fast user registration and log-in. With Keycloak integration, every user of Cloud Defense will be able to log in and each of them will be given a certain level of access based on the type of account they hold.
Backend/Frontend features
Another reason for integrating Keycloak into this project is to enable users to authenticate (single sign-on) using various existing platforms such as Facebook, Google, Linked In, GitHub, etc. After authorization, users do not need to log in to the system again on other devices (signed once, signed everywhere). This gives the users the convenience of not signing in every time they want to use Cloud Defense.
Load testing
Since the platform is likely to get a lot of traffic, we did load testing to determine the change in the system's behavior when dealing with an increased number of synchronous requests. The main goal was to determine whether the Server crashes when it is overwhelmed with requests. The system remained stable even when it had to deal with many requests.
Tools used to build, host, and test the system
Testing
Project was tested on the client’s side with the assistance of our QA engineer.
Hosting
Azure + Amazon: Deployment (was done on the client’s side)
We chose Azure and AWS because they are very reliable cloud infrastructure platforms and have enough resources to host and run applications like Cloud Defense.
Methodology of development
We used the Kanban methodology because it is the most effective one for balancing the quality of work and delivery time.
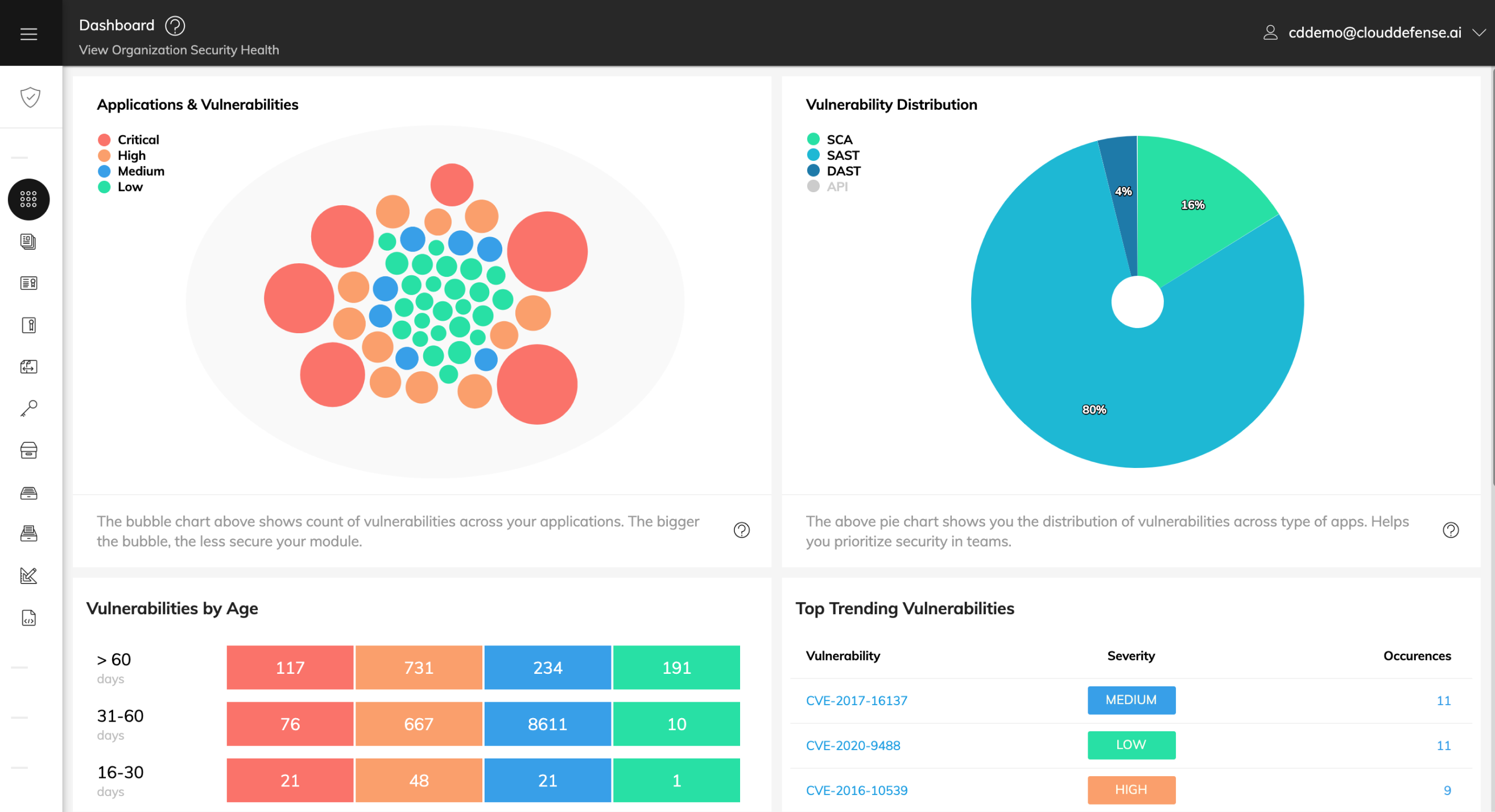
The top features created by us
Integrating ServiceNow
The principle of Jira software development. The primary role we played was to set tasks, control, and automate.
Single sign-on – Keycloak
Integration of Keycloak into the system was crucial since it enables users to securely sign in once using already existing services like GitHub, Google, and Facebook.
Serverless architecture
This is a scanning tool that helps verify security access for AWS services.
Online scanning:
When this feature is implemented into the system, it will be possible to scan projects from the web app; so there will be no need to use the CLI
Test scanner
A page (subproject) has been created that can use a special type of online vulnerability resource and send a report by mail. With this feature, users will be able to get regular emails about the vulnerabilities in their projects.
Rescan
This feature will enable users to rescan their applications without additional data entry.
Flexible charts
This feature makes it possible to move and resize charts to fit your needs
Binary tree
On the front end of this application, users can now view their system's vulnerabilities in the form of a binary tree to make interpretation much easier for them.
Schedule Report (in progress)
On the front end of this application, users can now view their system's vulnerabilities in the form of a binary tree to make interpretation much easier for them.
The most difficult
The integration of a serverless architecture into the system. It was challenging to implement a scanner that checks a feature for vulnerabilities, creates an image for it in Docker, runs this image through the GO language, and then receives the result and sends it to the Server for further transformation.
Details
Timeline
January 2021 - ongoing
Team
2 server part; 1 QA; 1 Front-end
Used Technologies

Angular
Material Design

Graphql

NgRx

Kubernetes

Java

Maven

Hasura
Micronaut

Bash script

Docker

Cube js

Go

PostgreSQL